A guide to AI prototyping for product managers
Discussions on AI in software development.
From
“Generative AI is in a bubble”
https://malwaretech.com/2025/08/every-reason-why-i-hate-ai.html
to
“All progress on LLMs could halt today, and LLMs would remain the 2nd most important thing to happen over the course of my career.”
https://fly.io/blog/youre-all-nuts/
to
“A vital shift is underway in software development, one that redefines how we build, but also who we are as developers.”
https://ashtom.github.io/developers-reinvented
And then, we forgot how to write HTML
You know “href”, don´t you?
Getting used to .env?
Before each prompt, direnv checks for the existence of a .envrc file (and optionally a .env file) in the current and parent directories. If the file exists (and is authorized), it is loaded into a bash sub-shell and all exported variables are then captured by direnv and then made available to the current shell.
AI as coding partner
https://martinfowler.com/articles/exploring-gen-ai/partner-with-ai-and-throw-away-the-code.html
Takeaway: ask the AI to explain the code.
Takeaway: use AI to generate unfamiliar (to me) utilities
Takeaway: use AI help to make test data more readable
Takeaway: refactor a function by providing an improvement idea to the AI
Takeaway: build understanding gradually, using AI to drive experiments and prototypes.
Takeaway: when in doubt, restart from scratch!
A real-world AI coding case sample
The internet is built on trust?!
“There are clear preferences that crawlers should be transparent, serve a clear purpose, perform a specific activity, and, most importantly, follow website directives and preferences.”
Etatistisches Missverständnis oder Etatistische Absicht?
Kleine Anfrage
der Fraktion der CDU/CSU
Politische Neutralität staatlich geförderter Organisationen.
Hier ein kleiner Auszug aus dem furchteinflößenden Dokument
https://dserver.bundestag.de/btd/20/150/2015035.pdf
Antwort und Einordnung auf verfassungsblog.de
https://verfassungsblog.de/offener-brief-kleine-anfrage-union/
Install Gitlab Runner in Docker Rootless for dind
Gitlab offers a well designed platform for open source projects. In the free version it is possible to use up to 400 min (?) runner time for CI-Jobs. It is also possible to connect self hosted gitlab-runners to power up you CI-Environment.
In my self administered environments I use a docker rootless setup most of the time.
How to register a gitlab-runner from within a docker-rootless environment?
1. Go to your group or project. Find the “runners” entry in the “Build” menu.
2. Add a new runner and copy the token to an editor or leave the page open for further reference (see step 7). Save everything.
3. SSH to your docker rootless host as “docker” user.
4. Find your userid by typing id
– Lets say it gives 1004
5. Start a gitlab-runner container using a socket mount from your users directory /run/user/1004
docker run -d --name gitlab-runner --restart always -v /run/user/1004/docker.sock:/var/run/docker.sock -v gitlab-runner-config:/etc/gitlab-runner gitlab/gitlab-runner:latest
6. Register the runner
docker run --rm -t -i -v /srv/gitlab-runner/config:/etc/gitlab-runner --name gitlab-runner gitlab/gitlab-runner register
7. If you are on gitlab.com simply add https://gitlab.com
as runner location. It will find your runner by entering the token you have copied in Step 2. User dockeras executer.
8. Now the runner should be connected. You can make use of by configuring it at your project/settings/ciconfig.
9. You can also add additional runner config under ~/.local/share/docker/volumes/gitlab-runner-config/_data/config.toml
GNU nano 6.2 /home/docker/.local/share/docker/volumes/gitlab-runner-config/_data/config.toml
concurrent = 1
check_interval = 0
shutdown_timeout = 0
[session_server]
session_timeout = 1800
[[runners]]
name = "my-runner"
url = "https://gitlab.com/"
id = 47413623
token = "XXX-your-token-here-XXX"
token_obtained_at = 2025-05-12T06:29:10Z
token_expires_at = 0001-01-01T00:00:00Z
executor = "docker"
[runners.cache]
MaxUploadedArchiveSize = 0
[runners.cache.s3]
[runners.cache.gcs]
[runners.cache.azure]
[runners.docker]
tls_verify = false
image = "docker:latest"
privileged = false
disable_entrypoint_overwrite = false
oom_kill_disable = false
disable_cache = false
volumes = ["/cache",,"/run/user/$ID_OF_YOUR_DOCKER_USER/docker.sock:/var/run/docker.sock"]
shm_size = 0
network_mtu = 0
10. Docker Compose
docker-compose.yml
services:
gitlab-runner:
image: gitlab/gitlab-runner:latest
restart: always
container_name: gitlab-runner
volumes:
- gitlab-runner-config:/etc/gitlab-runner
- /run/user/1004/docker.sock:/var/run/docker.sock
volumes:
gitlab-runner-config:
Leaving USA
Three prominent Yale professors depart for Canadian university, citing Trump fears.
Snyder ist einer der bekanntesten Historiker der Welt. Sein Buch Bloodlands ist wohl auch hier in Deutschland vielen bekannt.
Hier macht Timothy Snyder ein paar Bemerkungen über Freiheit und Empathie, 26.3.2025
https://www.youtube.com/watch?v=Rorpfw-SWhk
Vielleicht sind das tatsächlich die Dinge, die wir uns 2025 gegeseitig nochmal erzählen müssen?
Corona und der Laborverdacht
Schon am 24.01.2025 äußerte Christian Drosten in der Taz sich zum möglichen Ursprung des Corona Virus:
“…
Bei dem Sars-1-Ausbruch 2002/2003 hat es ein paar Jahre gedauert, aber dann kamen immer mehr Studien aus China, die wasserdicht gemacht haben, dass dieses Virus aus solchen Tieren kommt.
taz: Das hätten Sie hier auch erwartet?
Drosten: Ja, und ich muss sagen, je mehr Zeit vergeht, desto skeptischer werde ich. Verbietet die Staatsräson, dass daran gearbeitet wird? Mag sein. Die andere Erklärung wäre aber, dass da gar kein natürliches Virus war. Die Politik sollte nach all den Jahren deutlicher die Forderung an China stellen, jetzt wirklich zu beweisen, dass es aus der Natur kommt.
taz: Wenn Sie jetzt sagen, dass dieses Virus vielleicht doch aus dem Labor kam, wird das für Aufruhr sorgen.
Drosten: Das würde ich so direkt auch nicht postulieren. Es ist aber nicht dasselbe, wenn wir im Jahr 2020 den Beleg für einen natürlichen Ursprung noch nicht haben, wie wenn wir im Jahr 2025 diesen Beleg immer noch nicht haben.”
https://taz.de/Christian-Drosten/!6061896/
Jetzt am 14.03.2025 häufen sich die Hinweise, dass auch andere Experten schon länger einen Ursprung im Labor vermuten:
https://www.tagesschau.de/inland/bnd-coronavirus-ursprung-100.html
Designing Data Products
Top GitHub Libraries 2025
Herfried Münkler: Welt im Aufruhr! Die Ordnung der Mächte im 21. Jahrhundert.
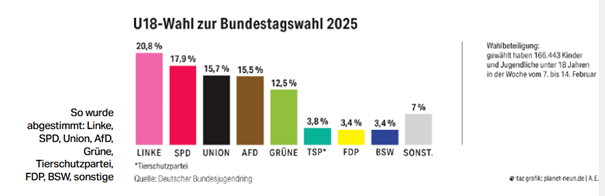
Überraschung bei der U18 Wahl
Wahlomat in a nutshell
Müssen Plattformen wie Facebook auch proaktiv Inhalte löschen?
Müssen Plattformen wie Facebook, TikTok, Instagram, YouTube und Co. ab Kenntnis illegaler Inhalte auch proaktiv nach sinngleichen Inhalten suchen und diese sodann ohne weiteren Hinweis ebenfalls löschen? Darüber wird ab dem 18.2.2025 der Bundesgerichtshof entscheiden.
Soziale Netzwerke als demokratische Kraft retten
Im digitalen Raum lenken wenige vorwiegend US-amerikanische und chinesische Tech-Konzerne1 Information und öffentliche Debatte. Deren Plattformen erlauben keinen ungehinderten Zugang: Denn Nutzende müssen für diesen Zugang persönlichste Daten preisgeben. Gleichzeitig filtern Algorithmen intransparent, was Nutzende zu sehen bekommen und was nicht – Algorithmen, die einzig den Gesetzen der Aufmerksamkeitsökonomie folgen, befreit von Gemeinwohlorientierung und journalistischen Qualitätsansprüchen. Mit einer Flut von Hass, Häme, Hetze und Desinformation zersetzen wenige Monopolplattformen unsere Demokratien und gefährden jeden Menschen2.